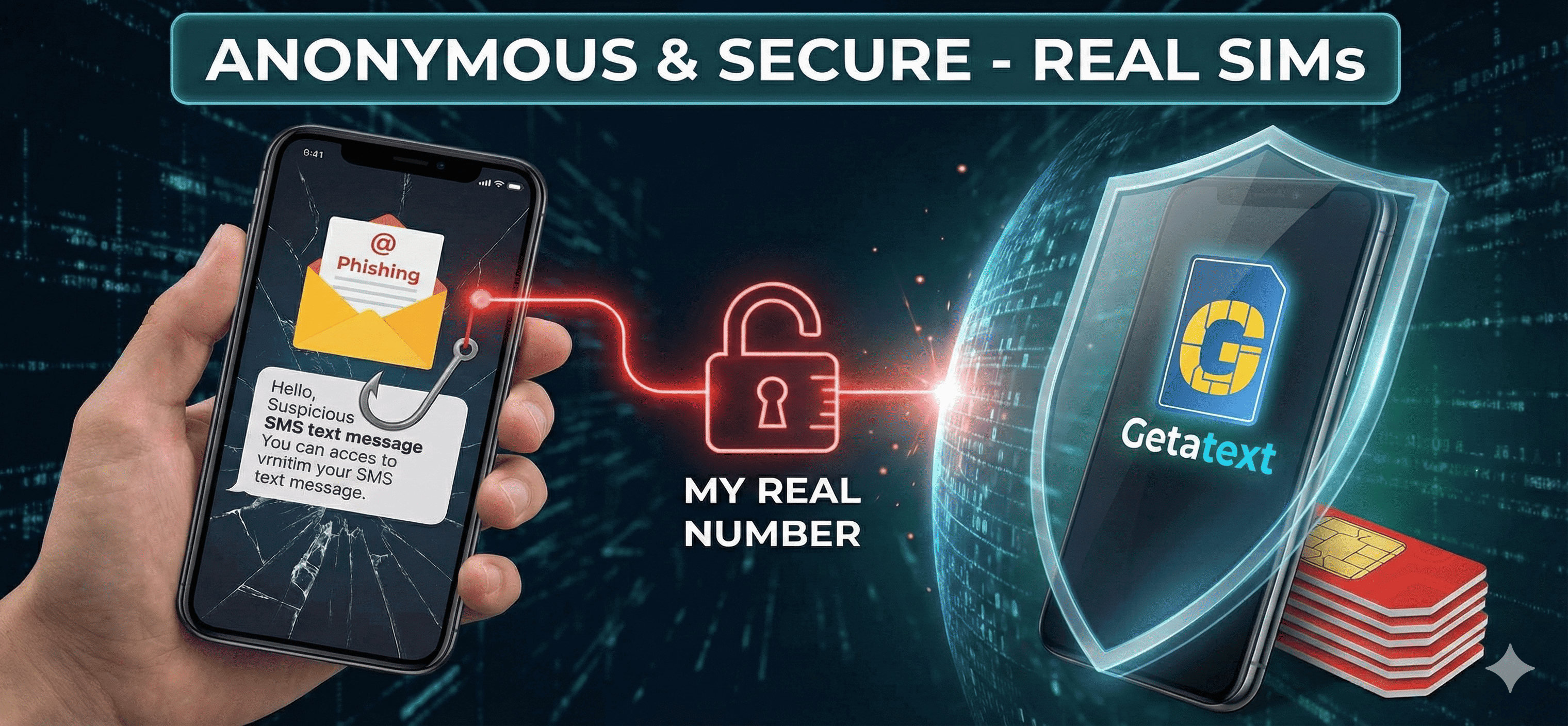
In today's digital landscape, your personal information is more valuable than gold. Cybercriminals are constantly evolving their tactics to steal your sensitive data, and two of the most prevalent methods are Phishing (via email) and Smishing (via SMS text messages). Understanding how these attacks work is the first step in defense, but the ultimate layer of security lies in decoupling your digital identity from your real-world identity using anonymous numbers.
The Mechanics of the Attack: Phishing and Smishing
Phishing is a social engineering attack where criminals masquerade as a trustworthy entity. You might receive an email that looks exactly like a security alert from your bank, a delivery notification from Amazon, or a login request from PayPal.
Smishing takes this threat to your pocket. It is phishing via SMS. Because people trust text messages more than emails, smishing has a frighteningly high success rate. The anatomy of these attacks usually involves:
- Urgency: "Your account will be suspended if you do not verify immediately."
- Fake Links: URLs that look legitimate but lead to a clone website designed to harvest your passwords.
- Data Extraction: Once you click, they ask for credentials, credit card info, and critically, your phone number.
Why Your Phone Number is the "Master Key"
Why do hackers want your phone number so badly? Because it is often the single point of failure for Two-Factor Authentication (2FA). If a hacker links your personal phone number to a compromised account, or targets you with a SIM-swapping attack, they can bypass your passwords entirely by intercepting your One-Time Passwords (OTPs).
Furthermore, once your real number is out on the dark web, you become a permanent target for spam, scams, and harassment. Changing your primary number is a massive headache—so the best strategy is not to expose it in the first place.
The Solution: Strategic Anonymity
To protect yourself, you should practice digital compartmentalization. You should never use your primary personal phone number for every single app, newsletter, or random website sign-up. By using anonymous numbers for these verifications, you create a firewall between potential attackers and your real life.
However, not all anonymous numbers work. Most services use VOIP (Voice Over IP) numbers, which are easily detected and blocked by major platforms like WhatsApp, Telegram, Google, and Tinder.
How Getatext.com Solves the Problem
This is where Getatext.com revolutionizes your privacy. We don't just offer random numbers; we provide the ultimate solution for secure verification.
Here is why Getatext is the superior choice for protecting your identity:
- Non-VOIP Technology: Unlike competitors, our numbers are not virtual landlines. They are treated by systems as genuine mobile subscriptions.
- Real SIM Cards: We utilize REAL SIM cards. This means when you request a number from us to receive an OTP, the service (be it Facebook, OpenAI, or a bank) sees a legitimate physical user. This guarantees the highest success rate for delivery.
- Cost-Effective Security: We believe privacy shouldn't break the bank. You can rent numbers for specific services at incredibly low prices, paying only for what you need.
- Disposable & Secure: Use a Getatext number to verify an account. If that account receives phishing texts or spam later, your personal phone remains silent and secure. You simply walk away.
Don't let your personal phone number become a vulnerability. mitigate the risk of phishing and keep your data safe by using Getatext.com for your next verification.